
Get your students unplugged and learning with these fun interactive activities that cover various topics and concepts using playing cards.
TestOut creates online, interactive courseware for students and teachers. Learn more about our courses.
This game doesn’t have a limitation on number of players, so you can include all your students in your class. It is a fun way to introduce the simple concept of attacking and defending cyber networks and systems to students using the “Candy Man,” or the designated Ethical Hacker, and the “Policeman,” or Cyber Defender. The Ethical Hacker sends signals to players signifying he’s trying to hack a system using one simple sign like a wink, nose tweak, lip pucker, and so forth. If the Ethical Hacker accidentally signals to the Cyber Defender, the game or round is over.
One game should take around 20 mins.
Remove all face cards except for one Ace (Ethical Hacker) and one King (Cyber Defender). If you have a larger group, you can add in another set of an Ace and King but use just one set when you play your first time, so you can get a feel for it.
Explain to the students what the Ace and King cards represent and that the number cards represent either the victims of hacks or individuals who cyber defenders protect.
If you have 20 students, you’ll have an Ace, King, and 18 number cards.
Shuffle and deal one card to each player. The players shouldn’t let others know what they have and should not indicate if they are the Ethical Hacker or Cyber Defender.
After all the cards are passed out, the sign from the Ethical Hacker conspicuously begins (in this case a wink). If one of the 18 number players sees the sign by the Ethical Hacker, they lay their card down and say, “I’ve been hacked.” The Ethical Hacker may pause and look around the group and try to deceive the Cyber Defender into thinking they’re just one of the number cards.
While cards are being laid down with players’ voices uttering, “I’ve been Hacked,” the Cyber Defender looks for the Ethical Hacker. If he thinks he knows, he says, “Got You!”, and the person he accuses lays down their card. If it’s an Ace, the round ends, and the Ethical Hacker was found. If it’s not, the game continues, and the person with that number card is out of the game until the next round.
Once someone is out by being hacked, they should avoid eye contact with the Ethical Hacker to not tip off the Cyber Defender.
You can play multiple rounds and/or keep score, depending on your time and a gauge of your students’ interest. Between each round, you could discuss the different types of attacks like phishing or a DNS attack.
This game helps students understand what it means for Hackers to look for vulnerabilities inside systems and how Cyber Defenders need to find those vulnerabilities in the systems they’re protecting. The act of searching on the part of the Cyber Defender and sneakiness on the part of the Ethical Hacker should hit home with your students and solidify this concept and help get them interested to keep learning about the exciting field of cybersecurity.
×Computers communicate to each other in binary numbers, 1s or 0s, also known as On or Offs. You can use face cards to teach this concept where a card faced up is a 1 and a card face down is a 0.
Decimal numbers are calculated using the actual number of a faced-up card while faced-down cards are also counted as 0s, just like in binary.
When you have a row of cards with some faced up and some faced down, you can show students how to compute both binary and decimal numbers by using 0s and 1s for binary and card numbers to compute decimals numbers.
Introduce students to these concepts using a simple set of four cards from the same suit:
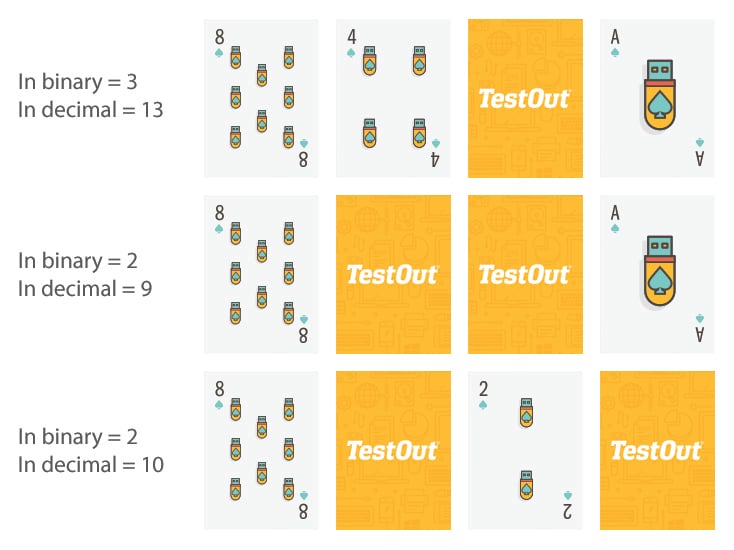
Using these four cards, you can use different variations and show how binary and decimal computations work. This video from Digital Schoolhouse provides an easy explanation.
Mathigon.org also has further discussion and resources, including a longer lesson, for using face cards to teach Binary.
×Students need to know that social engineering is a hacker’s way of deceiving and manipulating individuals into divulging personal information used for fraudulent purposes like stealing someone’s identity or using their information to steal their logins or other credentials and to access personal accounts like work and bank accounts.
This is a fun class game that can work with up to 20 students using one deck of cards. Each player starts the game with three lives and then the person with the lowest card loses a life after every round. This is a great way, as you explain the game, to compare it to social engineering such as how a card a player decides to pass to the next player in hopes of having a higher card is like someone determining what kind of personal information they’re willing to share online and how to spot a hacker performing social engineering.
In the game of Ranter Go Round, a player has counters (something like jelly beans or paperclips or pennies will work) that are considered lives. If you have 20 students, you’ll need 60 counters and you will then need to divvy them up to each student.
Cards are ranked, high to low, as follows:
A-K-Q-J-10-9-8-7-6-5-4-3-2-1. Remove any Jokers.
Ace is considered the “high” card of the game. This is an important aspect of the game to be explained.
The goal for each round is for students to avoid having the lowest card in the group or they lose a life.
Choose a student for the first round to be the dealer where he or she shuffles and then passes one card to each student. Only one card is passed out per player per round, and each player only has one turn. The remaining cards are placed in the center of the table or in a place accessible as one card will be drawn by the dealer per round.
The person to the left of the dealer starts the game. She or he examines the card and decides, depending on if it’s a high card, whether to keep it or pass it to the person to the left.
If chosen to pass it to the left, the student next to them must accept it unless they have an Ace or the high card. An Ace card is like the wild card of the game that everyone wants to get. If a student gets an Ace at the beginning of the round, and the student next to them passes them a low card, they get to lay down their Ace card in front of them and sit out the rest of that round and not worry about losing a life.
The next person to the left goes and decides to keep or pass their card, and the process continues until it gets back to the dealer. For this last turn, the dealer determines to keep his or her card or exchanges it for a card in the remaining deck. If an Ace card is drawn, the dealer must keep the other card.
At the end of the round, all students flip and show their cards. Whoever has the lowest card, loses a life. When a player loses all their lives, they are out of the game. If there’s a tie among players, all lose a life.
The dealer changes each round to the person on the left, the deck is reshuffled, and a new round begins.
After multiple rounds, the last two remaining players can 1) tie the game or 2) play one more round to determine the winner.
Between each round, you could teach students different Social engineering tactics a hacker will use. After a winner is determined, you can quiz the winner to teach the class what social engineering is.
Another competitive aspect you can add into the game is with a Poker element. Every time someone loses a life, they put it in a shared pot pile. At the end of the game, the winner gets the pot!
×This card game could be used as a full class period (1 hour) and is an engaging way to introduce students to Conditionals, a key concept in the world of computer programming.
House of Code, or specifically Code.org, provides a detailed lesson plan for teaching Conditionals with a traditional 52 Face card pack.
×With the advancement of Cloud computing, it has become a big part of our world, and a major technology practice and expertise that IT professionals work with every day. However, on-premise computing, using traditional networking and data storage, is still alive and well and necessary. In many or most cases, a hybrid model is best used for organizations across the globe.
This is an easy game to grab attention and have an engaging discussion on Cloud and on-premise computing.
Prep for this game essentially includes content to teach these concepts and a standard 52-card deck. You’ll need to understand the reasons why Cloud computing is the best option, why On-premise is best, and instances when both or Hybrid is best.
Only use the number of cards aligned with the number of students with one card per student in this game. Break the cards into 3 categories: High, Middle, and Low:
High Ranked Cards
Ace, King, Queen, Jack
Mid Ranked Cards
10, 9, 8, 7, 6
Low Ranked Cards
5, 4, 3, 2, 1
Before introducing the topic of Cloud, On-premise, and Hybrid computing, explain to the students the High, Mid, and Low Ranked cards.
Tell the students that a High Ranked card means that the person is valued higher than someone who’s Mid or Low.
Pass out the cards to students face down and ask them not to look at the card. Have the students stand up and place their card on their forehead with the card facing out for others to see.
Explain that you want the students not to talk but to walk around and treat the other students, using non-vocal cues, by the value of their card. If a student is a low ranking card, maybe they’ll get an eye roll. If they’re mid ranking, perhaps a subtle nod. A student with a high-ranking card might get a bow or salute.
After a few minutes, explain that high ranking cards represent Cloud Computing, mid ranking represent Hybrid, and low-ranking cards represent on-premise. Affirm the point that one should not assume Cloud is superior based on “face value.”
This is an engaging way to introduce students to this concept and begin your lesson.
×Take the number of students in your class and match it with the number of cards. Include just one Ace, King, Queen, and Jack and remove the other Ace, Kings, Queens, and Jacks from the deck.
Pass out the cards to the class. Ask students to indicate who have the lone Ace, Jack, Queen, and King cards.
Use this to start your discussion on Networking Topologies on the four main topologies:
Ace Card – Bus Topology
Jack Card – Star Topology
Queen Card – Ring Topology
King Card – Tree or Hierarchical Topology
Starting with the Ace card, introduce students to Bus topology and so on.
If you have room in your class for students to stand up and space out as a group a little, ask the class to form in groups using the person with one of the Ace, Jack, Queen, or King Cards as captains and ask them to line up in their respective topologies. In the example below, students line up in the Star topology with the captain in the middle.
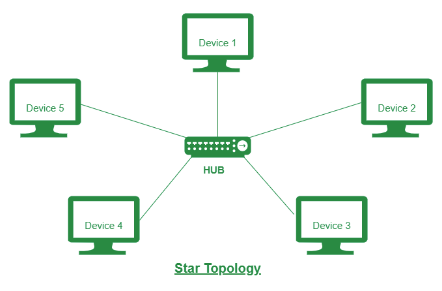
You then explain to the class how the Star topology works or ask the group to explain it to the class. As an attention getter, this game can be flexible to your teaching.
Feel free to add in few more cards for students to get if you want to teach a few more concepts like hybrid and mesh topologies.
×If you’ve ever played 52-card pick up, this is a prank game. You ask a friend if they’ve ever played it, and then if they say, “no,” you throw cards up in the air, and he or she must pick them up.
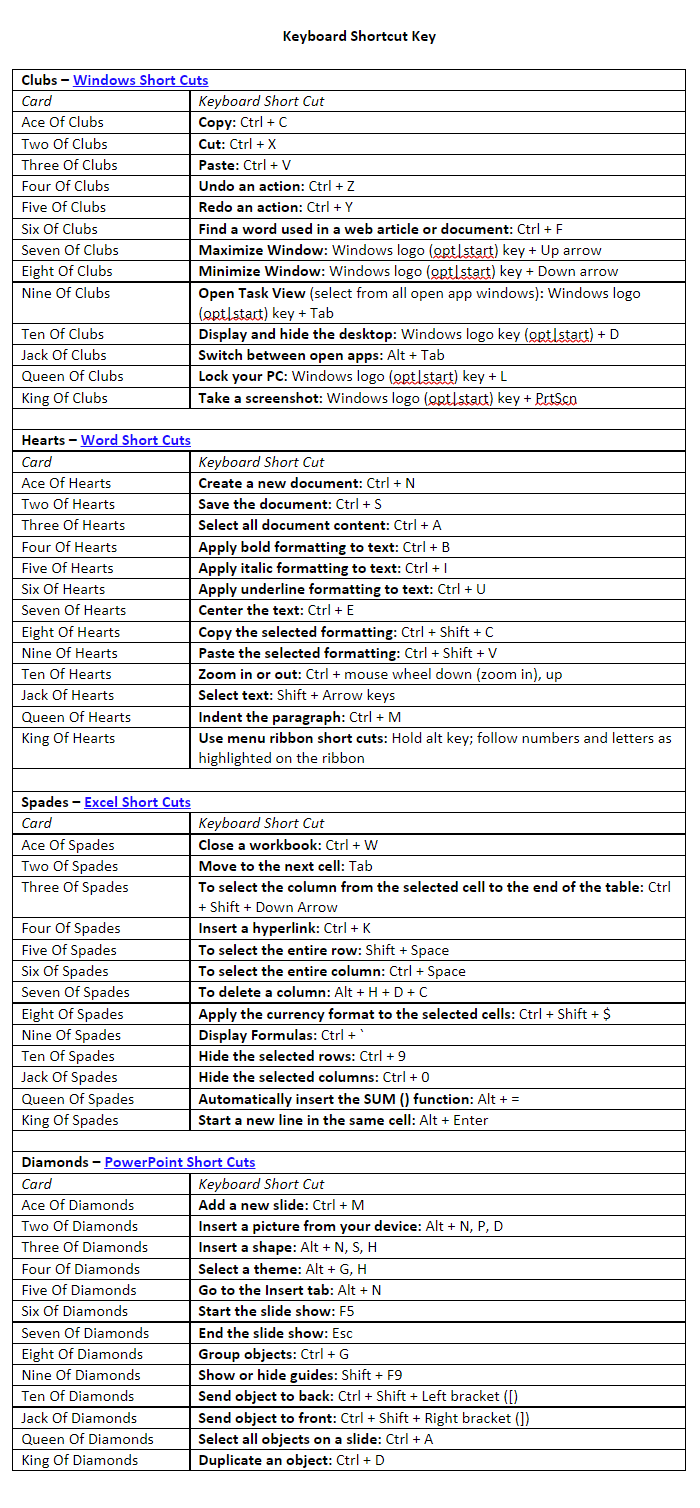
Most students probably have heard of it or have been pranked, but this game can be fun for getting attention and helping introduce students to keyboard shortcuts for Microsoft Windows, Word, Excel, and PowerPoint.
First, consider how you’ll play this game with how you’re teaching these subjects. If this is a survey class, and you’ll be covering all topics, you could use all 52 cards. If you’re covering one subject at a time, starting with Windows, for example, you could only pull the Club cards out of the deck and instead do a 13-card pick-up game.
This game works best when students have access to their computer or you are in your computer lab, so students can practice on Windows and the Office applications during the game and class discussion.
Remove the Joker card from the deck. With your students sitting down at their desks, tell them you’d like to play a card game. Take the deck of cards and scatter them across the classroom as you see fit.
For a 52-card game: Depending on the number of students you have, let’s say 15, you’d tell your students to pick up three cards each and that seven special students will pick up a fourth card.
For a 13-card game (or how you see fit. A 26-card game could cover two subjects): Tell the students to run and grab a card and that there’s only 13, so there won’t be enough for everyone. If you have prizes to motivate them to get out of their chairs, that can make it fun.
2) Have students pull up their computers. In the case you’re working in Excel that day, begin going through the Spades cards using any order you’d like from the Key. Ask who has Ace of Clubs. Then ask if they know the keyboard short cut for Copy. If they know, great, if not, you explain it, and move onto the next card/shortcut. You can take your time between each card to let students practice the short cut.
Depending on the level of your students and the topics you’re covering that day, this game can be adapted to you.
You can save the key in your LMS for students to reference or have it projected from your screen.
This is more of an attention getter than a card game, but it’s something students can associate with keyboard shortcuts, which will prove very beneficial in their careers!
 ×
×



Get your students unplugged and learning with these fun interactive activities that cover various topics and concepts using playing cards.
TestOut creates online, interactive courseware for students and teachers. Learn more about our courses.
Flip the cards below to learn more about each game. Detailed, printable instructions are included.
Introduce students to the concepts of cyber attacks and defense through the laugh-out-loud face card game, Candyman.
See Full InstructionsTeach students how computers communicate through binary numbers and decimals.
See Full InstructionsTeach students the impact of Social Engineering using the classic face card game, Ranter Go Round.
See Full InstructionsTeach students the importance of conditionals in programming and experience how they work through a hands-on card game.
See Full InstructionsTeach the pros and cons of Cloud computing and on-premise computing through this fun card and interactive attention getter game.
See Full InstructionsInteractively teach students the four main topologies using face cards, getting up from their desks and moving around the classroom.
See Full InstructionsPlay a game with a key that matches all 52 cards with keyboard shortcuts for Windows, Word, Excel, and PowerPoint.
See Full InstructionsCopyright © 2024 TestOut Corp. Copyright © CompTIA, Inc. All rights reserved. | Privacy Policy | Accessibility | License Agreement
Microsoft, MCA, Office, Excel, Word, and Windows are the trademarks of Microsoft. Cisco and CCNA are the trademarks of Cisco. Certified Ethical Hacker and CEH are the trademarks of the EC-Council. Neither TestOut nor CompTIA have any affiliation with any of these companies, and the products and services advertised herein are not endorsed by any of them.